Details
Joined devRant on 12/3/2016
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
-
Me: *Watching a movie*
Main Character: "Oh no, we have to hack the CIA to figure out how this machine works! Hacker girl, do the stuff"
Hacker Girl: "Consider it done!"
Hacker Girl: *Opens Linux bash*
Hacker Girl: *types 'mkdir Hack_CIA'
Hacker Girl: "They have two-factor authentication in place, this is going to be a hard one."
Hacker Girl: *Types 'cd Hack_CIA'*
Hacker Girl: "I'm in!"
Me: "..."
Friend: "Wow, so well done, so realistic!"
Me: *Dies*82 -
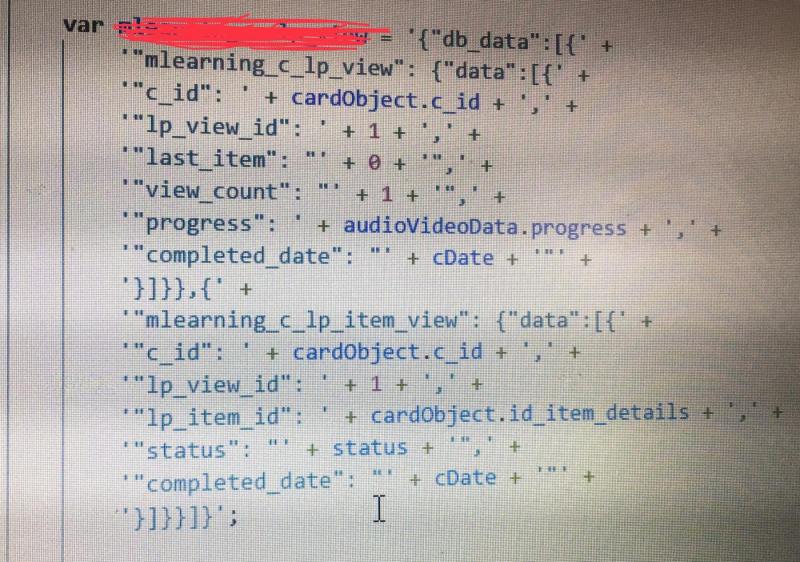
So I accidentally published my AWS keys to GitHub, stupid me. I realize this the next day.
$ git reset
$ git push
Reset keys in AWS
I was too late. Bot already stole the keys and started up 53 EC2 instances. Racked up $4000+ of compute time (probably Bitcoin mining, I'd assume)
4 weeks later, I finally have this shit disputed and settled.
Don't test with hardcoded keys. You WILL forget about them. Env vars always. That is all.30 -
I had a secondary Gmail account with a really nice short nickname (from the early invite/alpha days), forwarded to another of my mailboxes. It had a weak password, leaked as part of one of the many database leaks.
Eventually I noticed some dude in Brazil started using my Gmail, and he changed the password — but I still got a copy of everything he did through the forwarding rule. I caught him bragging to a friend on how he cracked hashes and stole and sold email accounts and user details in bulk.
He used my account as his main email account. Over the years I saw more and more personal details getting through. Eventually I received a mail with a plaintext password... which he also used for a PayPal account, coupled to a Mastercard.
I used a local website to send him a giant expensive bouquet of flowers with a box of chocolates, using his own PayPal and the default shipping address.
I included a card:
"Congratulations on acquiring my Gmail account, even if I'm 7 years late. Thanks for letting me be such an integral part of your life, for letting me know who you are, what you buy, how much you earn, who your family and friends are and where you live. I've surprised your mother with a cruise ticket as you mentioned on Facebook how sorry you were that you forgot her birthday and couldn't buy her a nice present. She seems like a lovely woman. I've also made a $1000 donation in your name to the EFF, to celebrate our distant friendship"31 -
You see a web, I see:
CLIENT: TCP SYN
SERVER: TCP SYN ACK
CLIENT: HTTP Get
SERVER: HTTP Response
...
CLIENT: TCP FIN
SERVER: TCP FIN ACK
All I’m saying is that this spider has a clear understanding of Transfer Control Protocol. 13
13 -
Professor : Explain deadlock and I will give you full marks.
Me:- You give me full marks and I'll explain deadlock.20 -
SSH'd into all the computers in college's lab and edited the bashrc to display "YOU ARE BEING WATCHED / YOU'VE BEEN HACKED" etc.
Everyone freaked out instantly.
Then edited my own bashrc file too so that no one realizes it's me.
I was surprised at how easy it was.8 -
I just came across this image
Even my grandma(80) can understand this :D
Source:
http://www.darwinbiler.com/about/ 5
5