Details
-
SkillsJs, Ruby, web development, SQL and a bit of other stuff
Joined devRant on 5/5/2016
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
-
Hope it's not a repost but this is brilliant... although putting it up in my office wouldnt change anything. Password123 was there before me and it'll be there after me.
 8
8 -
So the company behind gitkraken released their version of trello and all that I am interested in from all the features they show off, is really just how they made their vscode plugin to open up a browser like sidepanel, since all the requests for that to be possible, have been halted by the vscode team because there was issues or they declined it
Also what do you guys think of it? is it going to replace trello for you?
https://www.gitkraken.com/glo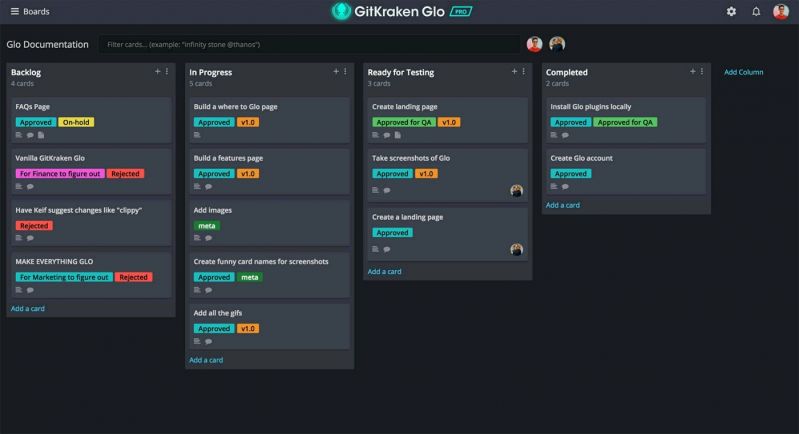 19
19 -
Aardwolf is very fun and i suggest y'all play it a bit if you're looking for better ways to slack off at work
$ telnet aardwolf.org 4000
*port 23 also works 23
23 -
Holy shit this is beautiful. Does anyone know is this theme is available for linux mint 18.3 or if there is something similar?
https://github.com/EliverLara/Ant 5
5 -
Just finished this great book! It was really entertaining and interesting 🙂
And it explained the advantages of DevOps and CI/CD in a very understandable way 😁
Do you have any other good recommendations for IT novels? 10
10 -
What's your programming background music?
I listen to classical music
These days mostly Chinese traditional
(No I'm not Chinese) 27
27 -
Q: How to catch an Elephant in the Africa
MATHEMATICIANS: hunt elephants by going to Africa, throwing out everything that is not an elephant, and catching one of whatever is left.
EXPERIENCED MATHEMATICIANS: will attempt to prove the existence of at least one unique elephant before proceeding to step 1 as a subordinate exercise.
PROFESSORS OF MATHEMATICS: will prove the existence of at least one unique elephant and then leave the detection and capture of an actual elephant as an exercise for their graduate students.
COMPUTER SCIENTISTS: hunt elephants by exercising Algorithm A:
1. Go to Africa.
2. Start at the Cape of Good Hope.
3. Work northward in an orderly manner, traversing the continent alternately east and west.
4. During each traverse pass,
1. Catch each animal seen.
2. Compare each animal caught to a known elephant.
3. Stop when a match is detected.
EXPERIENCED COMPUTER PROGRAMMERS: modify Algorithm A by placing a known elephant in Cairo to ensure that the algorithm will terminate.
ASSEMBLY LANGUAGE PROGRAMMERS: prefer to execute Algorithm A on their hands and knees.
ENGINEERS: hunt elephants by going to Africa, catching gray animals at random, and stopping when any one of them weighs within plus or minus 15 percent of any previously observed elephant.
ECONOMISTS: don't hunt elephants, but they believe that if elephants are paid enough, they will hunt themselves.
STATISTICIANS: hunt the first animal they see N times and call it an elephant.
CONSULTANTS: don't hunt elephants, and many have never hunted anything at all, but they can be hired by the hour to advise those people who do.
OPERATIONS RESEARCH CONSULTANTS: can also measure the correlation of hat size and bullet color to the efficiency of elephant-hunting strategies, if someone else will only identify the elephants.
POLITICIANS: don't hunt elephants, but they will share the elephants you catch with the people who voted for them.
LAWYERS: don't hunt elephants, but they do follow the herds around arguing about who owns the droppings.
SOFTWARE LAWYERS: will claim that they own an entire herd based on the look and feel of one dropping.
VICE PRESIDENTS OF ENGINEERING, RESEARCH, AND DEVELOPMENT: try hard to hunt elephants, but their staffs are designed to prevent it. When the vice president does get to hunt elephants, the staff will try to ensure that all possible elephants are completely prehunted before the vice president sees them. If the vice president does happen to see a elephant, the staff will:
1. compliment the vice president's keen eyesight and
2. enlarge itself to prevent any recurrence.
SENIOR MANAGERS: set broad elephant-hunting policy based on the assumption that elephants are just like field mice, but with deeper voices.
QUALITY ASSURANCE INSPECTORS: ignore the elephants and look for mistakes the other hunters made when they were packing the jeep.
SALES PEOPLE: don't hunt elephants but spend their time selling elephants they haven't caught, for delivery two days before the season opens.
SOFTWARE SALES PEOPLE: ship the first thing they catch and write up an invoice for an elephant.
HARDWARE SALES PEOPLE: catch rabbits, paint them gray, and sell them as desktop elephants.9 -
Problem saving emojis to your database? MySQL’s utf8 only allows you to store 5.88% of all possible Unicode code points. https://mathiasbynens.be/notes/...2
-
De-google your life
Search:
-qwant
-startpage
-searx
-duck duck go look up the founder
-yandex (putin botnet)
Mail
-cock.li
-ProtonMail
-Posteo
-Tutanota
-your own
Browsers
-https://kek.gg/i/3g2z6d.png (superior list)
-https://kek.gg/i/67YQQx.jpg (for furfags)
-https://wiki.installgentoo.com/inde...
/Web_browsers
Collaborative documents
-quip
-turtl
-ether pad (eg: notes.typo3.org or etherpad.net)
-microsoft office online (lol)
Image Upload/Edit
-kek.gg
Video sharing
-hooktube
-bitchute.com
-vid.me
-dtube.video
Social
-gnu social (for freedom loving patriots)
-mastodon (for proprietary loving gook pedos and sjws)
-gab.ai
-minds
-diaspora
Image Upload/Edit
-kek.gg
Google CDN avoidance
-Decentraleyes
Ad and script blocking
-uBlock Origin
Share links without gibbing clicks
-archive.is
Android
-droid-break.info
How to hosts file (lol, just block google bro):
-https://archive.is/gBJ8i
Reading:
-https://wiki.installgentoo.com/inde...
/Anonymizing_yourself#Fingerprinting
-https://wiki.installgentoo.com/inde...
/Firefox#Notable_add-ons
-https://panopticlick.eff.org77 -
-The oldest computer can be traced to Adam and Eve
-Yes, it was an apple
-But with an extremely limited memory
-Just one byte
-Then everything crashed5 -
A scammer called me today. They were saying that harmful files were moved to my computer and they needed to remove them. I don't think they are ever going to call me again.
S = scammer; M = me;
S: this is tech support we need access to your computer because we detected harmful files and need to remove them.
M: oh my! Hold on, let me go to my computer now. How can you access it?
S: we can just use RDP and delete the files. They are in a hidden folder that is encrypted so this Is the only way.
M: oh ok I believe you. Hm... it looks like my son only allows certain IP addresses to access our computers.. I don't know how to disable this so can you just email me your IP address?
S: Sure...
He then sends me his actual IP address... it doesn't even look like a proxy or VPN.
M: oh my I forgot that you need my password to login. It's really long and complicated... can I just email it to you?
S: Sure!!
I then tell him to hold on I have to find it that my "son" stored it somewhere.
At this time I'm taking a photo of my bare ass and attaching it to the email. I then say in the email "Please note what my job title is in my signature.. I just sent the FBI your name, phone number, email, and IP address. Please enjoy my bare ass, you'll see a lot of it in prison."23