Details
Joined devRant on 2/13/2018
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
-
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.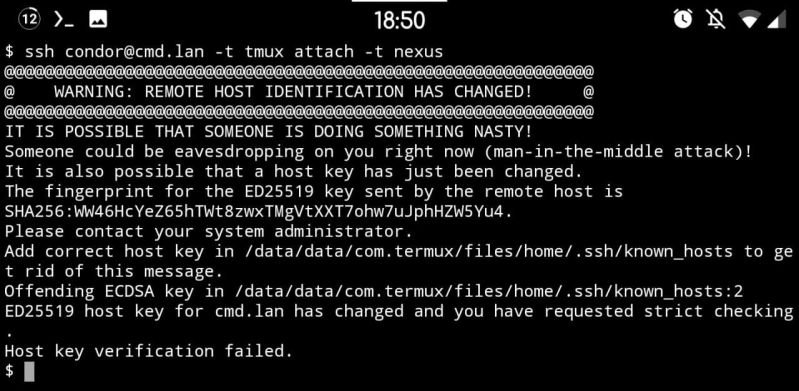 19
19 -
I'm working on a concept for an efficiency/speed focused networking project.
Any recommendations for low-level languages that support networking that can be run on both windows and Linux with relative easy?
Thanks in advance!5 -
I fucking hate this low level programming shit. The fucking buffer overflow attacks and the whole understanding of the system architecture just goes over my mind. Can anyone who has found relatively useful resources be kind enough to refer them to me so my stupid mind can understand that better?15
-
Here's an even meaner prank. Make it just a tad more difficult on them.
Set chrome in kiosk mode, so they can't switch out of the browser.
Unfortunately 'Alt + F4' still works, but they'd have to know that ahead of time.
And then kill off `explorer.exe` so they can't press the windows key.
You can either set this up as a bat, or you can do all of this from the Task Manager.
```
chrome --chrome-frame --kiosk "http://fakeupdate.net/win10/"
taskkill /f /im explorer.exe
```
And to really piss them off, set it up such that every time they reboot it just goes straight to the update screen
You can set Chrome to run as the Windows shell instead of explorer.exe. Just set the registry
```
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon Shell =
[chrome path]
```4
