Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
C'mon now guys, maybe he just don't really know it. I have better question tho: why take something you don't know?
-
 liketop557yYea guys pretty nice answers...
liketop557yYea guys pretty nice answers...
I'm still learning but thanks.
And yea I took it for the challenge and for learning purposes. -
Rather than posting here search Google for commonly known exploits for that Mac os version. Setup the Mac os in your local computer practice on it. Other than this best of luck
-
 liketop557yThank you guys for your constructive help!
liketop557yThank you guys for your constructive help!
You're not like the other trolls.
It's always about learning in penetration testing. -
I suggest running a nmap port scan scan for services to perform a banner grab provided that they aren't using ids like snort or anything banner grabs are noisy. Next if you can find the server version search to see if it had any vulnerabilities that allow rce i suggest looking in the online cve database or exploitdb
-
 Root771657yI suppose a screwdriver is out of the question?
Root771657yI suppose a screwdriver is out of the question?
Anyway. Start with nmap, scrape versions wherever you can, look for vulnerabilities.
Related Rants

 This is a view from a rooftop in NYC that I sometimes get the pleasure to work from. I really like the view an...
This is a view from a rooftop in NYC that I sometimes get the pleasure to work from. I really like the view an... Makes sense now
Makes sense now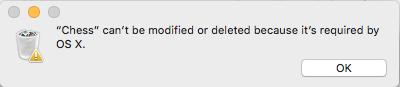 If you're wondering why your Mac is slow as sh*t, be advised that it's playing Chess during it's free time.
If you're wondering why your Mac is slow as sh*t, be advised that it's playing Chess during it's free time.
Hello together.
I need your help. Im a junior Pentester.
Tomorrow I need to pentest a Macintosh workstation but I have no idea where to start. Users can login via LDAP and I will do a white box pentest.
Any suggestions where to start?
question
pentest
macbook
pentester
mac